Fake Android coronavirus app reveals possible iPhone spyware
False Android coronavirus app reveals possible iPhone spyware

A new spyware entrada that uses both cryptocurrency and the coronavirus every bit lures may exist getting set to hit iPhone and Android users, co-ordinate to a new report from Trend Micro.
Tom'southward Guide did some further digging into the domain names and companies mentioned in the Trend Micro written report, and found information that blurs the line between legitimate online companies and possible criminal activity.
- The best Android antivirus apps
- iPhone SE 2020 unveiled: What y'all get for $399
The Android spyware apps tin steal Facebook messages, WhatsApp letters, text messages, contact lists, call logs, photos, and location and device information from infected phones.
The iOS apps' information-stealing capabilities are fewer, but Trend Micro thinks that "the apps may still be in development or incubation, possibly waiting for a 'correct time' to inject the malicious codes."
2 apps of these apps are yet bachelor in both the Google Play and iOS app stores, but Trend Micro noted that the apparent malware's "coding manner suggests that the cybercriminals behind this campaign are amateurs."
If yous're an Android user, you'll want to protect yourself with one of the all-time Android antivirus apps. There's no such antivirus software available for iPhones, only Apple tree told Trend Micro that the iOS "sandbox is able to detect and cake these malicious behaviors."
An apparently legitimate company
The apps seem to originate from a company called Concipit 1248, whose website proclaims it as the "1st Cashback Platform on Blockchain". The visitor offers a white paper explaining its business organisation model, and its executives seem to be a mix of Pakistani and Italian citizens. Concipit 1248 appears to be based in Estonia, and its website looks totally legit.
Only Concipit 1248 is associated with a website called Cashnow.ee. (The best antivirus software will cake admission to information technology.)
That in plow has a subdomain called "spy.cashnow.ee" that looks like a full cybercrime site, including a flashy groundwork animation that features the V for Vendetta mask and refers to "Project Spy 201" and "Target Mr. Anonymous."
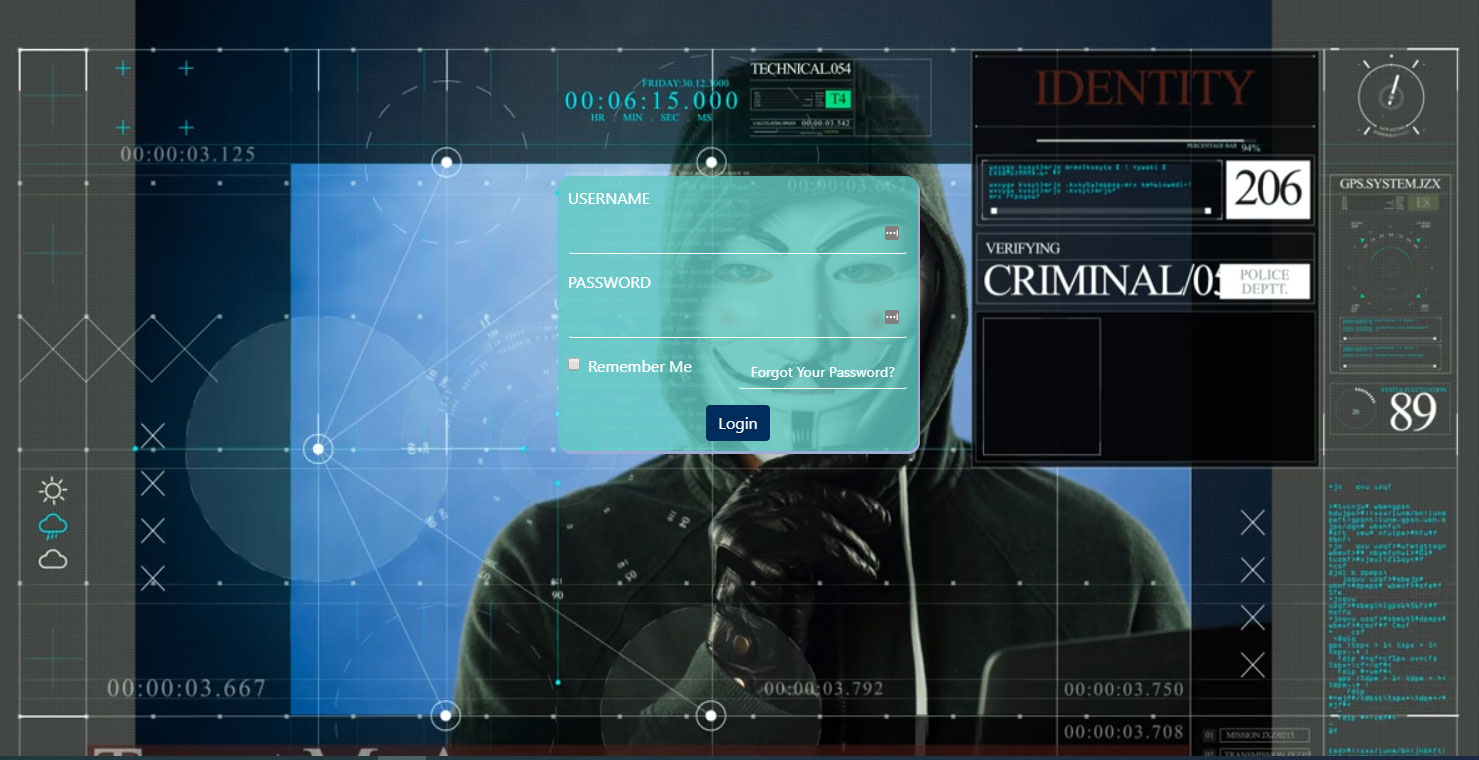
As a result, Trend Micro calls this whole performance Project Spy.
Concipit 1248 currently has 2 apps in both the Google Play and iOS app stores, called Concipit 1248 and Concipit Store.
The beginning has something to practice with the Ethereum cryptocurrency, while the second seems to exist a cash-dorsum platform for online shoppers. Both apps' self-descriptions are discussion salads of trendy tech-concern buzzwords.
Trend Micro examined the iOS version of the Concipit 1248 app and plant that it communicates with the "spyware.cashnow.ee" server. It's not articulate if Tendency Micro examined, or was enlightened of, the Android versions of those apps.
Unraveling a thread
The unraveling of this thread of threats began final month when Trend Micro looked at a bogus Android app called Coronavirus Updates. Tom'due south Guide couldn't find Coronavirus Updates in the official Google Play store, merely Trend Micro'due south report implied the app had been there at one point.
Coronavirus Updates steals all sorts of information from Android phones, every bit noted above. Similar the iOS version of the Concipit 1248 app, information technology also dials upwards to and logs into the aforementioned "spy.cashnow.ee" server.
Trend Micro establish that the "spyware.cashnow.ee" had also been used by earlier Android spyware apps, including a music-sharing app that appeared to be a false version of TikTok. That app is no longer available, just its developer was listed in Google Play as Concipit 1248.
Overlapping buying
Registry information for both the "concipit1248.com" and "cashnow.ee" domains is hidden behind privacy proxies, but Tom's Guide constitute a contact name and email accost for "cashnow.ee" listed on the Estonian domain registrar. ("EE" is the Estonian top-level domain suffix.)
The contact name for "cashnow.ee" matches that of the founder of Concipit 1248, as listed in the house'southward white newspaper, and also matches that of a 38-year-old man who is office of the management team of an Estonian firm called CashNow.
The contact email accost clearly refers to Concipit 1248. Tom'due south Guide sent it a message seeking comment on the Trend Micro report, and nosotros will update this story when we receive a reply.
Trend Micro noted that, "equally this is a group we have not observed before, we volition proceed monitoring this campaign for further developments."
Tom's Guide has to stress that these various companies and websites could exist completely legitimate and not involved in annihilation illegal. Even the "spyware.cashnow.ee" website could just be an ironic joke. But there'southward a lot of circumstantial testify to bespeak otherwise.
Source: https://www.tomsguide.com/news/ios-android-coronavirus-spyware
Posted by: coleforetump.blogspot.com


0 Response to "Fake Android coronavirus app reveals possible iPhone spyware"
Post a Comment